Inconsistent/ intermittent user permissions and login issues
問題
Users face intermittent permissions/ login issues. This can occur for all Atlassian applications the symptoms may include:
症状 1
Users are added/removed during every other user directory synchronization.
症状 2
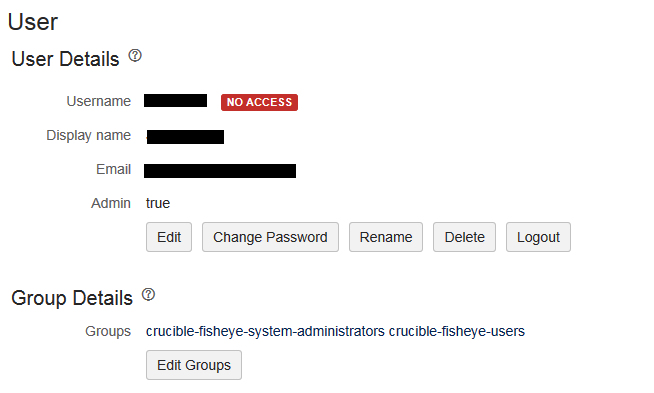
Users are show with permissions set correctly, however they can't login. For instance in FishEye/ Crucible you may see that the user has no access even though they belong to a group which has permissions.
原因
Atlassian Applications do not currently support connecting to load-balanced AD/LDAP servers. Synchronizing between AD/LDAP servers is not supported. Microsoft Active Directory does not replicate the uSNChanged attribute across instances. For that reason, we do not support connecting to different AD servers for synchronization.
Many companies have a single DNS entry (mydomain.mycompany.com) that points to a load balancer that directs traffic to one of many directory servers. (Or, some companies might use DNS round robin.) However, neither the use of DNS round robin nor use of an actual load balancer is supported by Atlassian applications – both approaches to load balancing direct traffic to different servers, which would violate this limitation.
Currently, Atlassian applications only supports connecting to a single directory server, not different (load-balanced) servers.
Related Product Suggestions:
CONFSERVER-23073 - 課題詳細を取得中... ステータス
JRASERVER-24133 - 課題詳細を取得中... ステータス
CONFCLOUD-23073 - Getting issue details... STATUS
FE-7017 - 課題詳細を取得中... ステータス
BSERV-11111 - Getting issue details... STATUS
回避策
These workarounds may not help depending on your exact scenario. Please make sure you test these workarounds before implementing them on your production instance. The only sure way to prevent this is to move away from a load balanced AD/ LDAP user directory.
症状 1
- Disable the incremental synchronization if possible.
- Attempt to connect directly to one of the LDAP nodes. You may gain some users and lose others depending on which node has the uSNChanged property.
- Delete and recreate the user directory.
- Move the internal directory to the top of the user directory list and add the affected users to a group created in the internal directory. Make sure you have a user in the internal directory you can login with otherwise you may get locked out.
- Move to a Delegated Directory type which will remove the synchronizations from the equation.
The caveat is that users must login for the first time via the UI in order to synchronise user groups and permissions. This means that if you have users who have access keys in their user profile, they will not be able to push using those access keys until they login via the UI or perform an HTTP(s) git operation.
症状 2
- Delete and recreate the user directory.
- Move the internal directory to the top of the user directory list and add the affected users to a group created in the internal directory.
ソリューション
Move away from a load balanced LDAP/ AD server.