ユーザー管理の目的
Can I use other authentication technologies for my User Directories - such as Google Apps, OAuth, Kerberos or SAML?
Out of the box, these technologies are not supported (with the exception of Google Apps in Atlassian Cloud - see the Atlassian Cloud section below for more information). The Atlassian Marketplace may have third party add-ons to add these authentication mechanisms in your applications.
There may also be other add-ons (outside of the Marketplace) that extend the capabilities of Atlassian Applications.
What are my options in Atlassian Cloud?
Google Apps can be used to provide users and groups to Atlassian Cloud. See the "Set Up Google Apps for your Site" page in our Documentation for more information about configuring Google Apps with your Cloud site. You can use Google Directory Sync to synchronise your LDAP directory to Google Apps, and then use the Cloud Connector to sync those users to your Cloud Site.
Please note that Google Directory Sync is both provided and supported by Google.
Common Scenarios
The following list a few common scenarios of layout for user management. Each example has at least one Atlassian application, along with an LDAP directory containing the business users and groups.
- An application that is "delegating" to another application relies on that application for its user management. For example, a Confluence that uses JIRA for user management is said to be delegating to JIRA.
- A downstream application is one that is affected by changes in the application it's delegating to. If Confluence is delegating to JIRA, Confluence is the downstream application - changes in JIRA may affect Confluence.
| シナリオ | Recommended use case | メリット | デメリット |
|---|---|---|---|
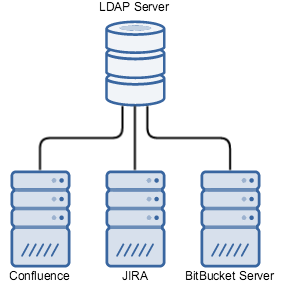
Direct connection from each Application to LDAP | Small-to-medium organisations with a large number of Atlassian applications |
|
|
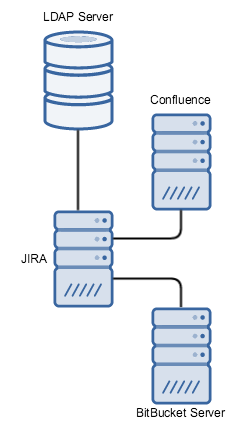
Applications delegating to JIRA which connects to LDAP | All organisations with a small number of applications
|
|
|
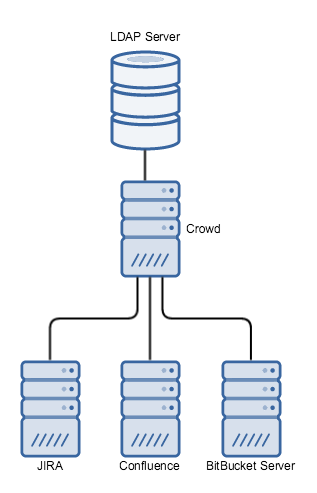
Applications delegating to Crowd, which connects to LDAP | All organisations with a large number of applications (both first and third party), or who require SSO |
|
|