セキュリティ管理
はじめに
キー ローテーションは追加のセキュリティ機能です。元のキーが侵害された場合に攻撃を受ける可能性の軽減に役立ちます。キーを定期的にローテーションできるため、キー侵害攻撃をさらに減らせます。キー ローテーションは既定では有効化されていません。有効にすることをお勧めします。
As an Atlassian Data Center administrator, you can manage the lifecycle of AES keys generated by Bitbucket Data Center through a set of REST APIs. These APIs allow you to manage keys either manually or programmatically.
AES キー管理 API
この API は、AES キーのローテーション、非アクティブなキーの取得、非アクティブなキーの削除のためのエンドポイントを提供します。以下に、URL、受け入れ HTTP メソッド、可能な応答コード、それらの意味など、各エンドポイントの詳細な説明を示します。
For full details of the API, visit https://developer.atlassian.com/server/bitbucket/rest/.
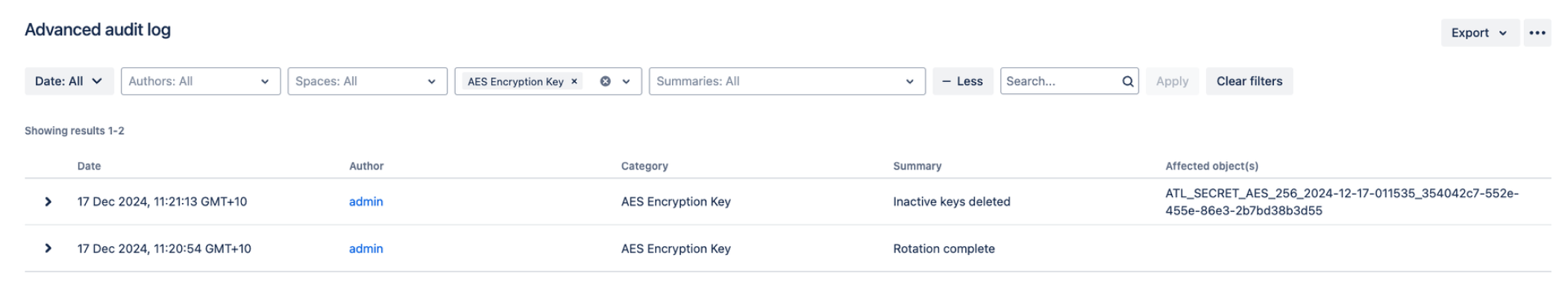
監査ログ
Key rotation and deletion events can all be found in the Bitbucket audit logs.
トラブルシューティングとヒント
認証
All endpoints require the user to have admin permissions. Ensure that you include the appropriate authorization headers with your requests.
エラー処理
500 応答 (内部サーバー エラー) が発生した場合は、アプリのログを確認して、不具合の原因を調査します。
401 (無許可) という応答を受け取ったら、自分の資格情報と権限を確認してください。
使用上の注意
<HOSTNAME> と <PORT> は、必ず DC インスタンスの実際のホストとポートに置き換えてください。