SSL または HTTPS 上での Jira アプリケーションの実行
アトラシアン アプリケーションでは SSL を使用できますが、SSL の構成はアトラシアン サポートの対象外です。そこで、サポートとして次を利用することをお勧めします。
- 証明書の変換に際してサポートが必要であれば、証明書の提供元のアトラシアン パートナーに相談してください。
- SSL の設定に関してサポートが必要な場合は、アトラシアン コミュニティで質問を作成してください。
既知の脆弱性によって SHA-1 は段階的に廃止されます。
この記事では、Apache Tomcat で HTTPS を設定することで Jira アプリケーションを SSL または HTTPS 上で実行する方法を説明します。この手順は Jira が通常の方法でインストールされている場合を前提としています。HTTPS 設定のすべてを網羅した手順の説明ではないため、ご利用の環境には適用されない場合があります。
このテーマの詳細は、次の記事をご参照ください。
Jira を SSL または HTTPS 上で実行する必要がある理由ユーザーがインターネットを経由して Web アプリにアクセスすると、ユーザーのコンピューターと企業の ISP (インターネット サービス プロバイダー) 間の中継点でユーザー名やパスワードが傍受される可能性が常にあります。そのため、HTTPS (HTTP over SSL) 経由でのアクセスを有効にして、パスワードを送信するページでこれを必須にすることが推奨されます。ただし、HTTPS を使用するとパフォーマンスが低下する可能性があることにご注意ください。
HTTPS を使用せずに Jira を実行すると、インスタンスが中間者攻撃やDNS リバインディング攻撃などに晒される可能性があります。インスタンスでは HTTPS を有効化することをお勧めします。
はじめる前に
サポート
アトラシアンのサポートは、SSL のサポートについては証明書を発行する認証局 (CA) に委ねます。このページにおける SSL 関連の説明は参考情報としてのみ提供されます。
Windows インストーラー
Windows インストーラーは、Tomcat を実行するために独自の JRE (Java ランタイム環境) Java プラットフォームをインストールします。SSL 証明書のアップデート時は、JRE のインストールする際に実行してください。
関連バグ
Jira 7.3 以降は、server.xml ファイルのプロトコルを誤って設定するバグ 2 つの影響を受けます。プロトコルを手動で設定することでこの課題を回避できます。
リバースプロキシの背後にある Jira
Jira が Apache のようなリバースプロキシの背後にホストされている場合の詳細については「SSL によって Jira と Apache を統合する」をご参照ください。
新しい接続の追加
SSL などの新しい接続を追加する際に、Jira 設定ツールは接続の詳細を含むエントリを server.xml ファイルに保存します。このエントリは特殊文字を処理するプロパティを含まないため、手動で追加する必要があります。このプロパティがなければ Jira は適切に機能しないため、これは必須の操作です。以降で必要な手順を説明します。詳細についてはこちらをご覧ください。
安全性が低い BKS-V1 キーストア形式
BouncyCastle ライブラリで提供される BKS-V1 キーストア形式にはセキュリティの脆弱性があるため、ご利用の Jira インスタンスでは使用しないことをお勧めします。詳細情報
Java キーストアの生成
お客様の SSL 証明書を保存する Java キーストア (JKS) を作成する方法について説明します。SSL 証明書は、Jira で SSL 通信を行うためには必須のものです。SSL 証明書は一般的に次の 2 つの種類に区分されます。
| 証明書 | 説明 | 使用環境 | 手順 |
|---|---|---|---|
| 自己署名証明書 | 認証局によるデジタル署名がない証明書です。Web サーバー証明書の正当性を確認する方法です。自分自身が自己名で署名します。 | テスト用、開発用、その他内部向けサーバーのみ | 1-13 |
| CA 署名証明書 | 認証局 (CA) のデジタル署名によって正当性が確認された証明書です。これにより、ブラウザやクライアントは証明書に信用を置くことが可能になります。 | 本番環境用サーバー | 1-19 |
信用のおけるサードパーティー認証局 (CA) が発行したデジタル証明書により、お客様の Web サイトがお客様の会社を正当に代表するものであることが証明され、お客様の会社の実在が認証されます。多くの CA では単にドメイン名のみを認証する証明書を発行しますが、VeriSign などでは、お客様の事業活動の存在、ドメイン名の所有権の存在、証明書使用に関するお客様の権限などを証明する高度の認証を提供しています。
CA の一覧は、ここをご覧ください。よく知られた認証局の例を次に示します:
当社としては、CA で署名された証明書の利用を推奨いたします。
Portecle をお客様のサーバーにインストールできない、またはコマンド ラインの利用をご希望の場合は、以下の「コマンド ラインによるインストール」セクションをご参照ください。
Portecle アプリをダウンロードして、Jira を実行するサーバーにインストールします。
このアプリケーションはサードパーティー製であり、アトラシアンではサポート対象外です。
適切な権限を持って実行できるように、アプリを管理者として実行します。また、
<JAVA_HOME>変数が Jira で使用する Java と同じバージョンを示していることを確認します。詳細については、「JAVA_HOME の設定」を参照してください。Linux/Unix サーバー上で実行している場合は、以下のようにサーバーに接続する際に X11 を転送することで GUI を利用できます。
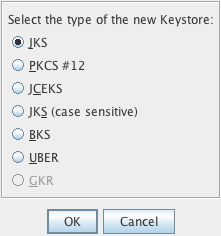
ssh -X user@server- [Create a new Keystore] を選択します。
- [JKS] 形式を選択して [OK] をクリックします。
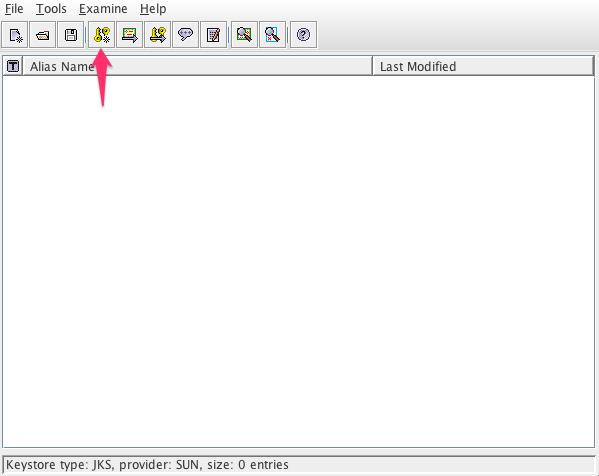
- [Generate Key Pair] を選択します。
- [Key Algorithm] では [RSA] を、[Key Size] では [2048] を選択します。
- [Signature Algorithm] が [SHA256withRSA] となっていることを確認します。「既定の SSL 暗号化が弱すぎることについてのセキュリティ ツールからの報告」をご参照ください。
以下の例のように証明書の詳細を編集して [OK] を選択します。
[Common Name] はサーバーの URL と一致している必要があります。一致しない場合はエラーがブラウザに表示されます。
- 証明書のエイリアス名を選択します。例:
jira - キーストアのパスワードを入力します。既定のパスワードは通常
changeitです。 - キー ペアの生成が成功した旨のメッセージが表示されます。
前のステップと同じパスワードが使用されていることを確認して、キーストアを
<Jira_HOME>/jira.jksに保存します。[ファイル] > [キーストアの保存] を選択して保存できます。自己署名証明書を使用する場合は、「Jira 設定ツールを利用した Web サーバーの設定」に進んでください。それ以外の場合は次の手順に進みます。
- 証明書の正当性を確認するために認証局に対して署名を依頼する証明書署名要求 (CSR) を生成する必要があります。これを行うためには、証明書上で右クリックして[CSR の生成] を選択します。CSR ファイルを
<Jira_HOME>/jira.csrに保存します。 - CSR を署名のために認証局に送信します。認証局からは、署名済み証明書 (CA 応答) および CA のルート証明書/中間証明書のセットが返送されます。
- [Import Trusted Certificate] でルート証明書と中間証明書の両方 (もしくは片方) をインポートします。証明書ごとにこの手順を繰り返します。
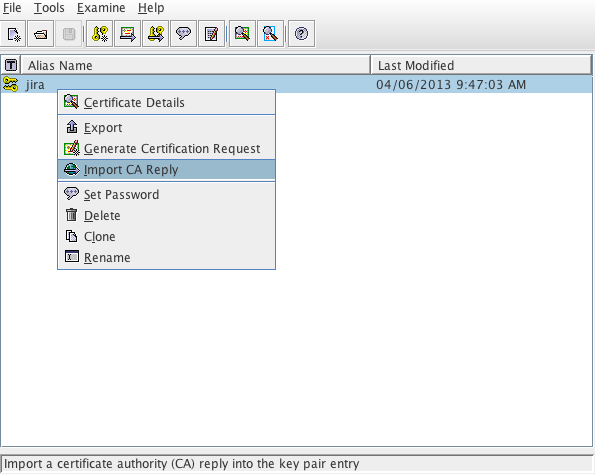
jira証明書で右クリックして [Import CA Reply] を選択し、署名付き証明書のインポートを開始します。- 認証局から提供された証明書 (
jira.crt) を選択します。CA 応答のインポートが完了したという通知が届きます。 - 結果を [ツール] > [キーストア レポート] で確認します。証明書はルート証明書の子ノードとして表示されます。
- キーストアを保存し、次のセクションに進みます :
Jira 設定ツールを利用した web サーバーの設定
Jira での SSL 暗号化設定の最後の手順として、Jira 設定ツールを利用して Web サーバーを設定します。Jira 設定ツールの詳細は、「Jira 設定ツールの利用」をご覧ください。
- 次のように Jira 設定ツールを実行します。
- Windows: コマンド プロンプトを開いて、Jira インストール ディレクトリの
binサブディレクトリにあるconfig.batを実行します。 Linux/Unix: コンソールを開いて、Jira インストール ディレクトリの
binサブディレクトリにあるconfig.shを実行します。このコマンドは「No X11 DISPLAY 変数が原因で Jira アプリケーション設定ツールを起動できなかったのは、設定エラーによるもの」に記載のエラーで失敗する場合があります。その場合は、この記事の回避策をご参照ください。
- Windows: コマンド プロンプトを開いて、Jira インストール ディレクトリの
- [Web サーバー] を選択します。
スクリーンショット: Jira 設定ツール — [Web サーバー] タブ 各フィールドに次のように入力します :
フィールド 値 ポートの制御 通常は初期設定のままとします。必要に応じてポート番号を変更することもできます。詳細は「Jira の TCP ポートの変更」をご覧ください。 プロフィール プロファイルとはプリセットされた Web サーバー動作設定です。次の 4 つの値から選択できます。 - 無効
- HTTP のみ
- HTTP および HTTPS (HTTP を HTTPS へリダイレクト)
- HTTPS のみ
Jira を HTTPS 上で実行する場合は、[HTTP & HTTPS] または [HTTPS] を選択する必要があります。
Jira を HTTPS 上で実行するが、ユーザーが HTTP 経由でも Jira アクセスできるようにする場合は、[HTTP & HTTPS] を選択してください。この場合、HTTP 経由で Jira にアクセスするユーザーは HTTPS のアドレスにリダイレクトされます。
HTTP ポート 通常は初期設定の
8080のままにします。必要に応じてポート番号を変更することもできます。詳細は「Jira の TCP ポートの変更」をご覧ください。[プロファイル] で [HTTPS のみ] を選択した場合はこのフィールドは無効になります。
HTTPS ポート 通常は初期設定の 8443のままにします。必要に応じてポート番号を変更することもできます。詳細は「Jira の TCP ポートの変更」をご覧ください。Keystore パス 証明書のキーストアの場所を指定します。これは、キーストアを保存した際に生成された場所で、
<Jira_HOME>/jira.jksです。Keystore パスワード キーストアのパスワードを指定します。自己署名証明書を生成した場合は、このパスワードは証明書を生成して保存したときにキーおよびキーストアに設定したパスワードです。 Keystore エイリアス キーストア内のそれぞれの項目はエイリアスで区別されます。証明書について jiraを使用することを推奨します。- 無効
- [Check Certificate in Key Store (キーストアの証明書をチェックする)] を選択して、次の項目を確認します。
- キーストア内に証明書が存在すること。
- キーストアのパスワードが有効であること。
- キー エイリアスを使用してキーを見つけられること。
- 変更を保存します。
新しい接続の追加時に、設定ツールには特殊文字を許可するプロパティが含まれないため、それらを server.xml ファイルに手動で追加する必要があります。方法の詳細についてはこちらの記事をご参照ください。
高度な設定
同一ホストにおける複数のインスタンスの実行
同一ホストで複数のインスタンスを実行する場合は、address 属性を <Jira_INSTALLATION>/conf/server.xml ファイルで指定します。既定ではコネクタは利用可能なすべてのネットワーク インターフェイス上でリッスンしており、同一の既定ポート上で実行されるコネクタ間の衝突を防止するためにアドレスを指定する必要があるためです。address 属性の設定の詳細については、Apache Tomcat ドキュメントの「The HTTP Connector」をご確認ください。
コマンド ラインを使用したインストール
ステップ 1.キーストアを作成します
Java キーストアを生成します。
<JAVA_HOME>/keytool -genkey -alias jira -keyalg RSA -keystore <Jira_HOME>/jira.jks姓名 (first and last names) の部分には、サーバーの URL から「https://」を除いたもの (jira.atlassian.com など) を指定します。
- パスワードを入力します。
手順 2 のパスワードを使用して、署名のための CSR を生成します。
<JAVA_HOME>/keytool -certreq -alias jira -file /output/directory/csr.txt -keystore <Jira_HOME>/jira.jksCSR を署名のために認証局に送信します。認証局からは、署名済み証明書と CA のルート証明書または中間証明書が返送されます。
証明書が署名されていない場合は、「Keystore で Tomcat を更新する」までスキップします。
ルート証明書、または中間証明書をインポートします。
<JAVA_HOME>/keytool -import -alias rootCA -keystore <Jira_HOME>/jira.jks -trustcacerts -file root.crt認証局から返送された署名済み証明書をインポートします。
<JAVA_HOME>/keytool -import -alias jira -keystore <Jira_HOME>/jira.jks -file jira.crtキーストア内に証明書が存在することを確認します。
<JAVA_HOME>/keytool -list -alias jira -keystore <Jira_HOME>/jira.jksこれは
PrivateKeyEntryである必要があります。異なる場合、証明書のセットアップが正常に完了していません。次に例を示します。jira, Jan 1, 1970, PrivateKeyEntry, Certificate fingerprint (MD5): 73:68:CF:90:A8:1D:90:5B:CE:2A:2F:29:21:C6:B8:25
ステップ 2.Keystore で Tomcat を更新する
- 編集する前に、
<Jira_INSTALL>/conf/server.xmlのバックアップを作成します。 HTTPS コネクタを編集し、キーストアを示すパラメーターを含めます。
<Connector relaxedPathChars="[]|" relaxedQueryChars="[]|{}^\`"<>" port="8443" protocol="org.apache.coyote.http11.Http11NioProtocol" maxHttpHeaderSize="8192" SSLEnabled="true" maxThreads="150" minSpareThreads="25" enableLookups="false" disableUploadTimeout="true" acceptCount="100" scheme="https" secure="true" sslEnabledProtocols="TLSv1.2,TLSv1.3" clientAuth="false" useBodyEncodingForURI="true" keyAlias="jira" keystoreFile="<Jira_HOME>/jira.jks" keystorePass="changeit" keystoreType="JKS"/>適切なパスを
<Jira_HOME>に入力して、必要に応じてポートを変更します。組織が最新の TLS バージョンをサポートしていない場合は、以前のバージョンへフォールバックできます。次のように変更します。
sslEnabledProtocols="TLSv1.2,TLSv1.3"to
sslEnabledProtocols="TLSv1,TLSv1.1,TLSv1.2,TLSv1.3"HTTP コネクタを編集し、HTTPS コネクタへリダイレクトするようにします。
<Connector relaxedPathChars="[]|" relaxedQueryChars="[]|{}^\`"<>" acceptCount="100" connectionTimeout="20000" disableUploadTimeout="true" enableLookups="false" maxHttpHeaderSize="8192" maxThreads="150" minSpareThreads="25" port="8080" protocol="HTTP/1.1" redirectPort="<PORT_FROM_STEP_1>" useBodyEncodingForURI="true"/><PORT_FROM_STEP_1>が適切な値に変更されていることを確認します。この例では8443です。- 変更を
server.xmlに保存します。 HTTPS へのリダイレクトを使用する場合 (推奨)、
Jira_INSTALL>/WEB-INF/web.xmlファイルを編集し、ファイルの末尾に次のセクションを追加してから、</web-app>を閉じます。この例では、添付ファイルを除くすべての URL が HTTP から HTTPS にリダイレクトされます。<security-constraint> <web-resource-collection> <web-resource-name>all-except-attachments</web-resource-name> <url-pattern>*.jsp</url-pattern> <url-pattern>*.jspa</url-pattern> <url-pattern>/browse/*</url-pattern> <url-pattern>/issues/*</url-pattern> </web-resource-collection> <user-data-constraint> <transport-guarantee>CONFIDENTIAL</transport-guarantee> </user-data-constraint> </security-constraint>- 変更内容を保存して Jira を再起動します。
また、Jira 設定ツールで「HTTP と HTTPS」プロファイルを選択して、HTTP URL から HTTPS URL へユーザーをリダイレクトすることもできます。
特定のページのみを HTTPS へリダイレクトしたい場合は手動で行う必要があります。
- Jira 設定ツールで「HTTPS のみ」プロファイルを選択して設定を保存します。
- HTTP URL を対応する HTTPS URL にリダイレクトする Web サーバー上に
htaccessファイルを作成します。
トラブルシューティング
上記にある通り Portecle を用いて生成した自己署名キーを使用する場合の、トラブルシューティングの TIPS をいくつか紹介します。
ブラウザに「https://localhost:<port number>」と入力したときに「Cannot establish a connection to the server at localhost:8443」のようなメッセージが表示される場合は、logs/catalina.out ログ ファイルでエラー メッセージを探します。ここでは発生する可能性があるいくつかのエラーとそれぞれの説明を紹介します。