Configuring a Delegated Authentication Directory
The username must be the same in the Crowd Delegated Authentication directory and in the LDAP directory. If a user is renamed in LDAP, Crowd will automatically rename the user in the Delegated Authentication directory.
Delegated Authentication directories do not allow you to browse the LDAP data. The directory delegates user authentication to LDAP, but to be able to list users and groups, you will need to add them to the directory. See more details in the Next Steps section of this page.
On this page:
Example of using a Delegated Authentication Directory
You can set up a simple group configuration in Crowd for use with Confluence and other Atlassian products, while authenticating your users against the corporate LDAP directory. You can also avoid the performance issues which might result from downloading large numbers of groups from LDAP.
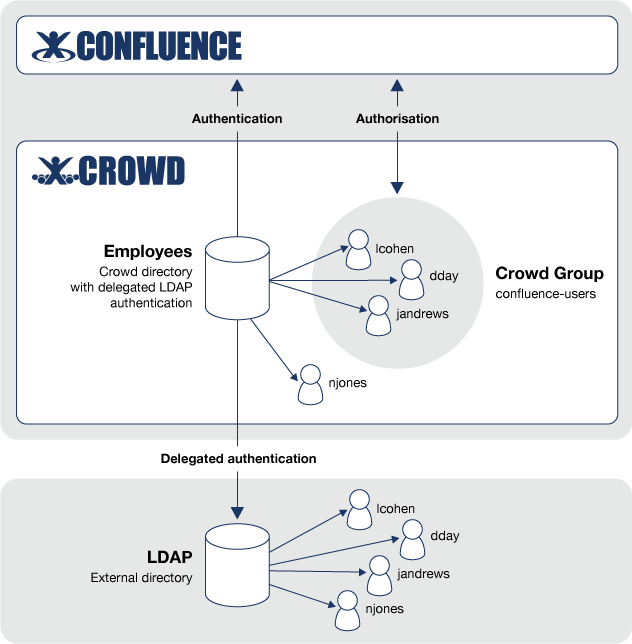
The diagram below gives a conceptual overview of delegated LDAP authentication. This example assumes that you have:
- The Confluence application integrated with Crowd.
- A Crowd Delegated Authentication directory called 'Employees' which contains the group 'confluence-users'.
- An LDAP directory containing all your employees and their authentication details (e.g. username and password).
設定手順
Before setting up a new Delegated Authentication Directory, please review to the notes on LDAP object structures in the page about LDAP connectors.
To configure a Delegated Authentication directory:
- Crowd Administration Console にログインします。
- Click the Directories link in the top navigation bar. The Directory Browser will open.
- Click the Add Directory link and then select the Delegated Authentication button.
- Complete the configuration information required on each of the tabs to finish setting up the directory.
If a user logs in successfully via LDAP authentication but does not yet exist in Crowd, Crowd will automatically add them to the Delegated Authentication directory. You will then need to add the user to any necessary groups, to allow them to access applications where group membership is required. If you have enabled the "Synchronize Group Memberships" option, groups and group memberships from LDAP will be automatically imported each time a user authenticates.
次のステップ
After configuring your new directory:
- Map the directory to the appropriate applications.
- Consider how you would like to add your users to Crowd's Delegated Authentication directory. There are a few options:
- Manually add the users to the Crowd directory.
- Use Crowd's Directory importer to copy your LDAP users into your Delegated Authentication directory.
- Let Crowd do it for you, at login time by enabling the Synchronize User Details option when you configure the directory.
関連トピック