SAML authentication fails with Received SSO request for user, but the user does not exist in Bitbucket Data Center
プラットフォームについて: Data Center のみ - この記事は、Data Center プラットフォームのアトラシアン製品にのみ適用されます。
この KB は Data Center バージョンの製品用に作成されています。Data Center 固有ではない機能の Data Center KB は、製品のサーバー バージョンでも動作する可能性はありますが、テストは行われていません。サーバー*製品のサポートは 2024 年 2 月 15 日に終了しました。サーバー製品を利用している場合は、アトラシアンのサーバー製品のサポート終了のお知らせページにて移行オプションをご確認ください。
*Fisheye および Crucible は除く
要約
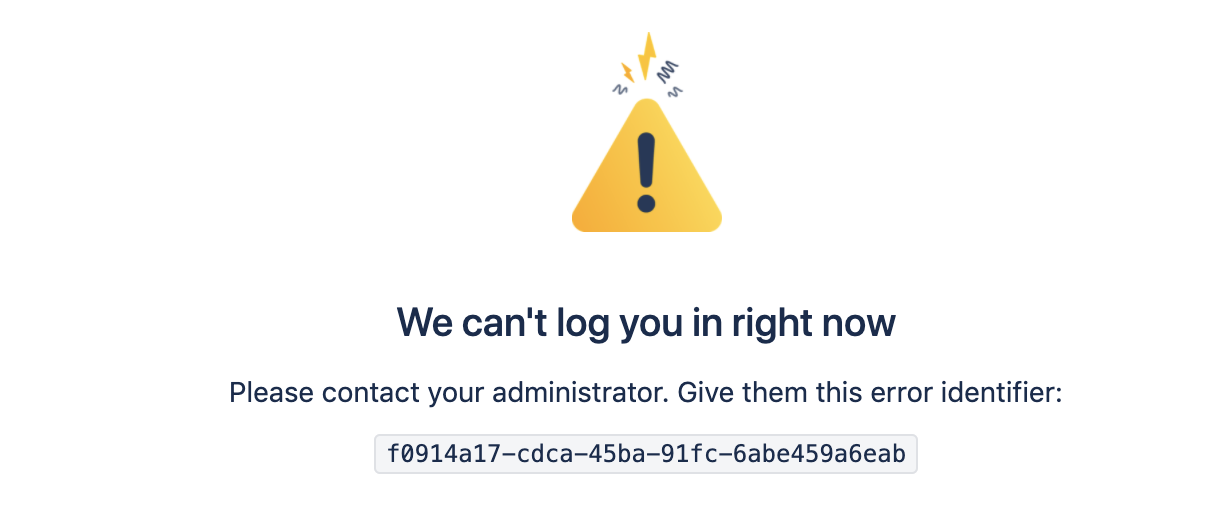
SSO SAML integration for Bitbucket Data Center with IDP fails with the below error - We can't log you in right now. Please contact your administrator. Give them this error identifier:
in the logs, We see the below errors -
2021-08-18 13:11:18,299 ERROR [http-nio-7990-exec-1] @VS5T83x791x77x0 X.X.X.X,127.0.0.1 "POST /plugins/servlet/samlconsumer HTTP/1.0" c.a.p.a.i.w.f.ErrorHandlingFilter [UUID: f0914a17-cdca-45ba-91fc-6abe459a6eab] Received SSO request for user <username or email>, but the user does not exist
com.atlassian.plugins.authentication.impl.web.usercontext.AuthenticationFailedException: Received SSO request for user <username or email>, but the user does not exist
at com.atlassian.plugins.authentication.impl.web.saml.SamlConsumerServlet.lambda$doPost$2(SamlConsumerServlet.java:112)環境
Bitbucket Data Center 7.14, 7.21
SSO SAML Integration with IDP (Google IDP, Azure AD etc.,)
診断
- Verify if Username Mapping is correctly set to ${NameID} in SAML configuration Bitbucket. You can refer to Error 500 and null pointer on a try to login with SAML connector for Bitbucket Data Center for more details on username mapping parameter.
Verify the SAML responses from your Browser by following the steps documented in How to view SAML responses in your browser for troubleshooting. You will see a similar SAML assertion response from your IDP for NameID
<saml2:Subject> <saml2:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">user@mydomain.com></saml2:NameID> <saml2:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"><saml2:SubjectConfirmationData InResponseTo="ONELOGIN_f47f48d6-351b-4eaf-bc34-f43d55f656c0" NotOnOrAfter="2021-09-01T10:43:46.713Z" Recipient="https://bitbucketdc713.mycorp.com/plugins/servlet/samlconsumer"/></saml2:SubjectConfirmation> </saml2:Subject>In this case, email id <user@mydomain.com> is sent in SAML response to Bitbucket. Bitbucket looks for <user@mydomain.com> as the username to process authentication requests.
- Get the user id from the Name ID format of the SAML response and verify if Bitbucket contains the user with a username matching the Name ID field.
原因
Bitbucket performs certain validations to verify if the user specified against NameID from SAML response exists in Bitbucket matching username. Suppose the NameID field from the SAML response returns <Email ID> and the username for the user in Bitbucket is set to <firstnamelastname> (for example) and not Email ID. In that case, there is a mismatch of usernames causing the issue.
ソリューション
Make sure the username matches the NameID format in Bitbucket for SAML authentication to be successful. This can be configured in the IDP SAML configuration to send a username (instead of an email address) in response to Bitbucket. If the IDP doesn't support configuring usernames, the next alternative is to change the usernames in Bitbucket.
To configure source attribute in IDP SSO SAML configuration for Azure AD,
- Login to the Azure portal and navigate to application SSO configuration ( Enterprise Applications → Your application → Set up single sign-on)
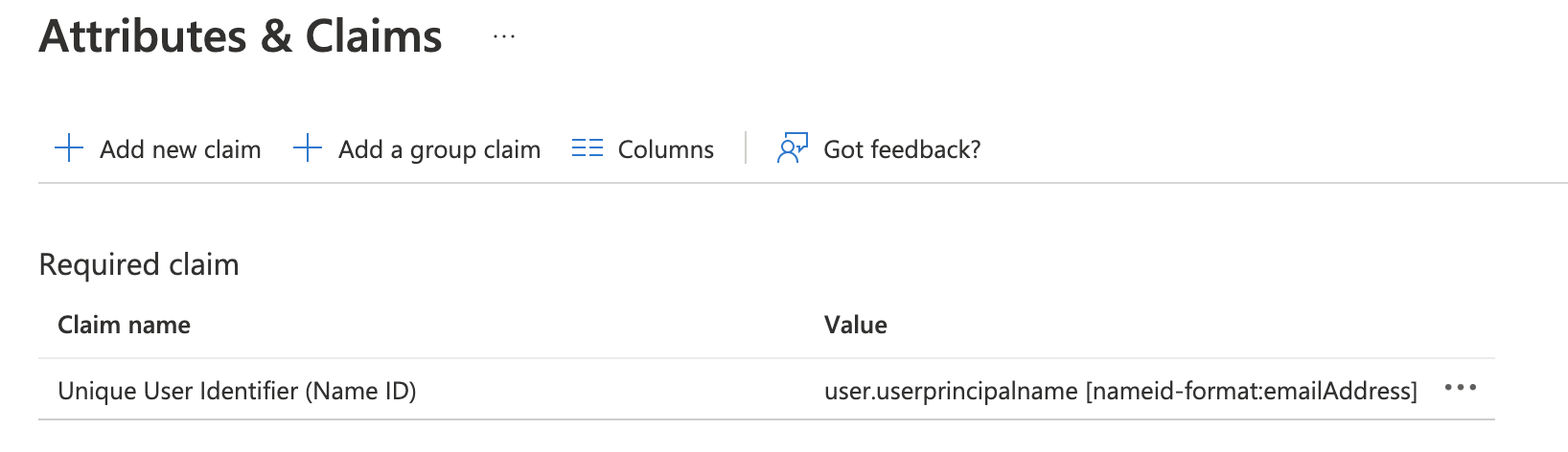
- Navigate to Attributes & Claims and click Edit
- Click on Unique User Identifier (Name ID).
Edit Unique User Identifier (Name ID) Value
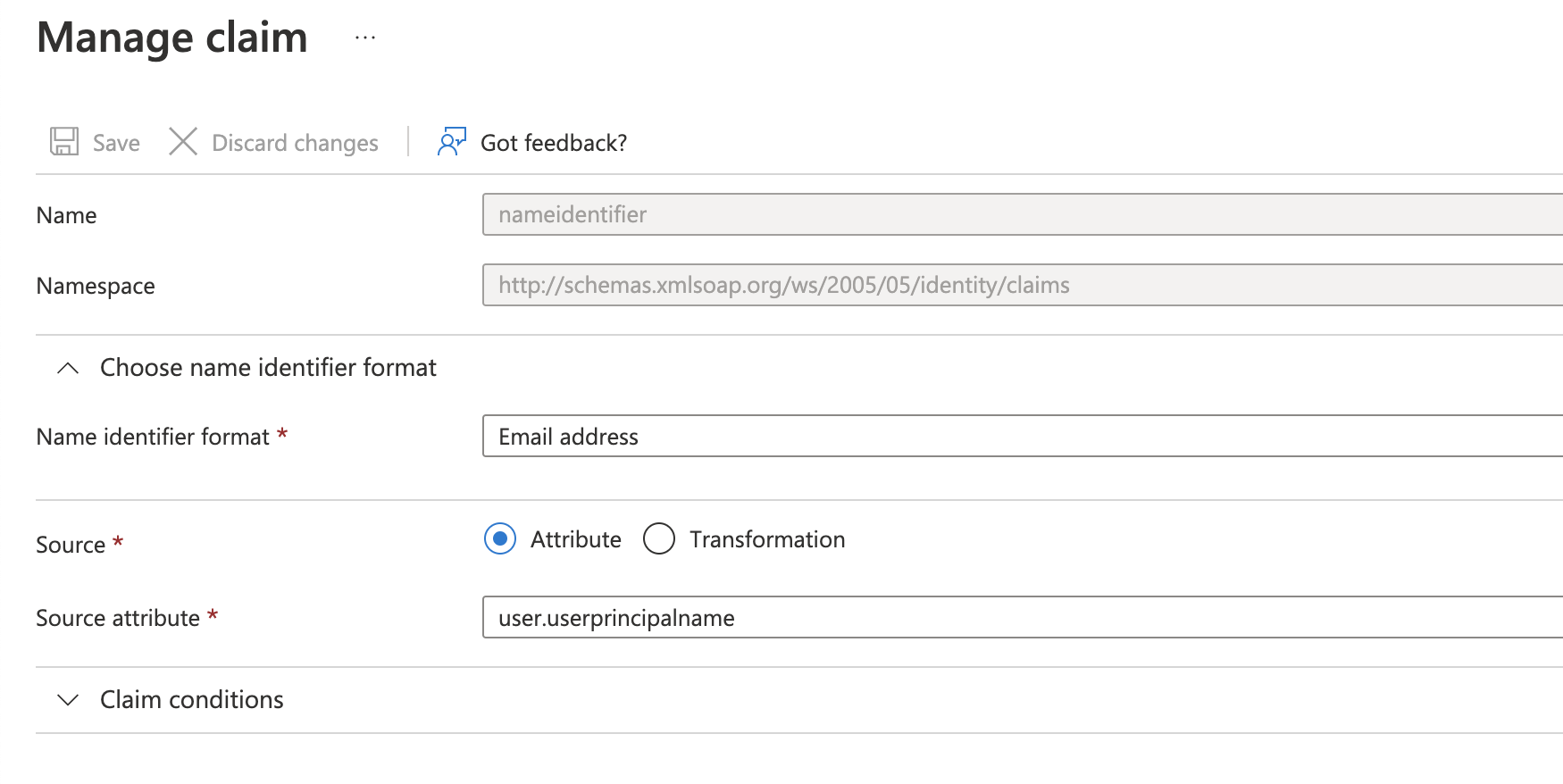
By default, the source attribute is set touser.userprincipalnameattribute. This is the Email ID attribute in Azure AD. Azure AD sends the user's email ID as a NameID identifier in SAML response to Bitbucket.Prior selecting
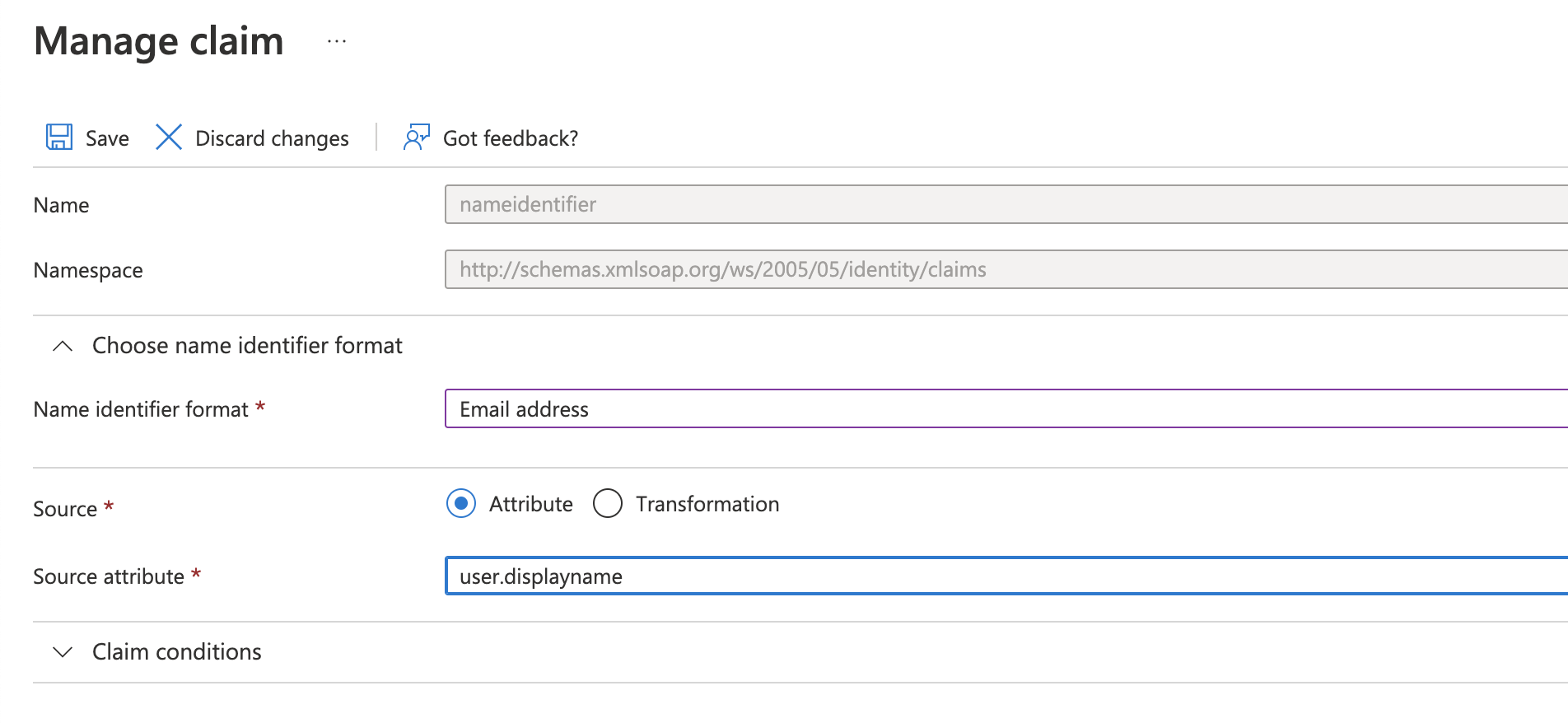
user.userprincipalnameas the Source Attribute, please make sure that the values of this field match the usernames in Bitbucket. Otherwise, select some other attribute i.e.user.onpremisessamaccountname- To change the source attribute from EMail ID to username, set the Source attribute to
user.displayname.This sends the username as a NameID identifier in SAML response to Bitbucket.
Please note that the navigation steps may differ in other IDPs, but the attributes can be changed under Attributes, Claims. If there is no option to set the attribute, the changes will be made in Bitbucket to match the username.
Additionally, if you are working with JIT provisioning and groups are used, you will have to make sure the specific group in Bitbucket has , at least, Bitbucket user permission.