How to enable and configure HTTP Strict Transport Security (HSTS) response header on Confluence
プラットフォームについて: Server および Data Center のみ。この記事は、Server および Data Center プラットフォームのアトラシアン製品にのみ適用されます。
Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Fisheye および Crucible は除く
HSTS enabled by default on Confluence 8.1.1 and later versions
Using the steps on this page to enable HSTS in Confluence 8.1.1 and later will cause the application to fail. Make sure you're following the appropriate steps for your Confluence version.
要約
For Confluence 8.1.1 and later
From Confluence 8.1.1, HSTS will be enabled by default on all HTTPS-capable sites. HSTS can be configured using Recognized System Properties.
Apache Tomcat 9’s HttpHeaderSecurityFilter provides the implementation for HSTS, and you can gain a better understanding of the configuration options by reading the Apache Tomcat 9 Configuration Reference.
Note that we've limited the parameters that can be configured to avoid breaking core functionality such as displaying images and previews.
For Confluence 8.1.0 and earlier
According to HTTP Strict Transport Security (HSTS) RFC (RFC 6797), HSTS is a mechanism for websites to tell browsers that they should only be accessible over secure connections (HTTPS).
This is declared through the Strict-Transport-Security HTTP response header. To enable it, you need to either configure a reverse proxy (or load balancer) to send the HSTS response header, or to configure it in Tomcat.
If using NGINX, refer to HTTP Strict Transport Security (HSTS) and NGINX. On Apache, you may use the mod_headers module to set response headers.
If you would like to configure it directly on Tomcat, refer to the steps below.
ソリューション
- Edit the <Confluence Install folder>/conf/web.xml file
Search for the following filter definition:
<!-- <filter> <filter-name>httpHeaderSecurity</filter-name> <filter-class>org.apache.catalina.filters.HttpHeaderSecurityFilter</filter-class> <async-supported>true</async-supported> </filter> -->Uncomment the block above to enable it. To know more about this filter check the Tomcat documentation
- Here you have two options:
- Option 1 is for the case you are using Confluence without any other application linked to it:
Customize the filter by adding parameters as follows:
<filter> <filter-name>httpHeaderSecurity</filter-name> <filter-class>org.apache.catalina.filters.HttpHeaderSecurityFilter</filter-class> <async-supported>true</async-supported> <init-param> <param-name>hstsEnabled</param-name> <param-value>true</param-value> </init-param> <init-param> <param-name>hstsMaxAgeSeconds</param-name> <param-value>31536000</param-value> </init-param> <init-param> <param-name>antiClickJackingOption</param-name> <param-value>SAMEORIGIN</param-value> </init-param> </filter>Ensure to set the antiClickJackingOption parameter using the value SAMEORIGIN, otherwise, pages that contain iFrame can stop working after enabling HSTS.
Option 2 is for the case you have other applications linked to Confluence, and these applications are exhibiting Confluence's content:
Customize the filter by adding parameters as follows:<filter> <filter-name>httpHeaderSecurity</filter-name> <filter-class>org.apache.catalina.filters.HttpHeaderSecurityFilter</filter-class> <async-supported>true</async-supported> <init-param> <param-name>hstsEnabled</param-name> <param-value>true</param-value> </init-param> <init-param> <param-name>hstsMaxAgeSeconds</param-name> <param-value>31536000</param-value> </init-param> <init-param> <param-name>antiClickJackingOption</param-name> <param-value>ALLOW-FROM</param-value> </init-param> <init-param> <param-name>antiClickJackingUri</param-name> <param-value><confluence-base-url>,<other-base-url>,<other-base-url></param-value> </init-param> </filter>Ensure to set the antiClickJackingOption parameter using the value ALLOW-FROM, and add antiClickJackingUri parameter replacing the parameter value by Confluence base URL and other applications base URL split by commas.
- Option 1 is for the case you are using Confluence without any other application linked to it:
-
Ensure the <async-supported> line is always above the <init-param> ones as shown in both options above. Otherwise, you may hit XML validation errors if that is enabled directly on the context or by the system property STRICT_SERVLET_COMPLIANCE
Next, search for this block:
<!-- The mapping for the HTTP header security Filter --> <!-- <filter-mapping> <filter-name>httpHeaderSecurity</filter-name> <url-pattern>/*</url-pattern> <dispatcher>REQUEST</dispatcher> </filter-mapping> -->Uncomment the mapping above and save the file
Restart Confluence so the modifications are applied
If you are running Data Center, then make sure to apply the same steps on all nodes of the cluster.
検証
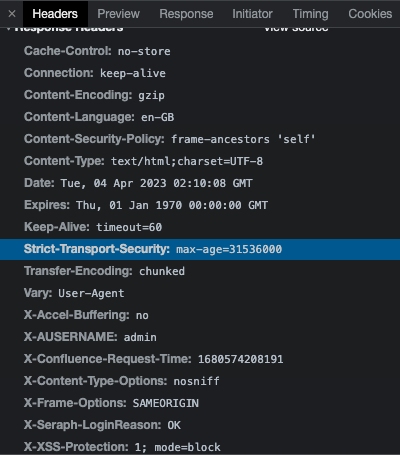
The easiest way to check is by launching the Chrome Devtools, clicking into the "Network" tab and looking at the headers tab. You will see something similar below:
Alternatively, run the below curl command:
curl -svo /dev/null https://<CONFLUENCE_BASEURL>/login.action --insecure 2>&1 | grep -i Strict-Transport-SecurityNote: The '–insecure' option is used to disable SSL certificate verification. This is necessary if the domain is using a self-signed or invalid SSL certificate.
注意:
- HSTS configuration will not work properly in Confluence 8.0.1 and 8.0.2: CONFSERVER-81829 - Getting issue details... STATUS
参考資料
HTTP Strict Transport Security on Wikipedia
HTTP Strict Transport Security on IETF
Strict-Transport-Security on MDN
HTTP Header Security Filter on Apache Tomcat 9 Configuration Reference