Jira server Base URL health check fails
Platform Notice: Data Center Only - This article only applies to Atlassian products on the Data Center platform.
Note that this KB was created for the Data Center version of the product. Data Center KBs for non-Data-Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
The Base URL Health Check ensures that Jira can access its own Base URL. In Jira 7.1 and above, gadget charts are created using Javascript in the browser instead of server-side with Java. This change resulted in significant performance improvements because the server no longer has to process everything, and the browsers can handle some of it. As a result, Jira now requires that the server can connect to itself, which is different from how it operated previously.
Impact
Gadget titles showing as __MSG_gadget.xxxxxxx, __MSG_gadget.activity., __MSG_gadget.filter, _MSG_gadget.project.title_ and so on, as per the example below:
For example:
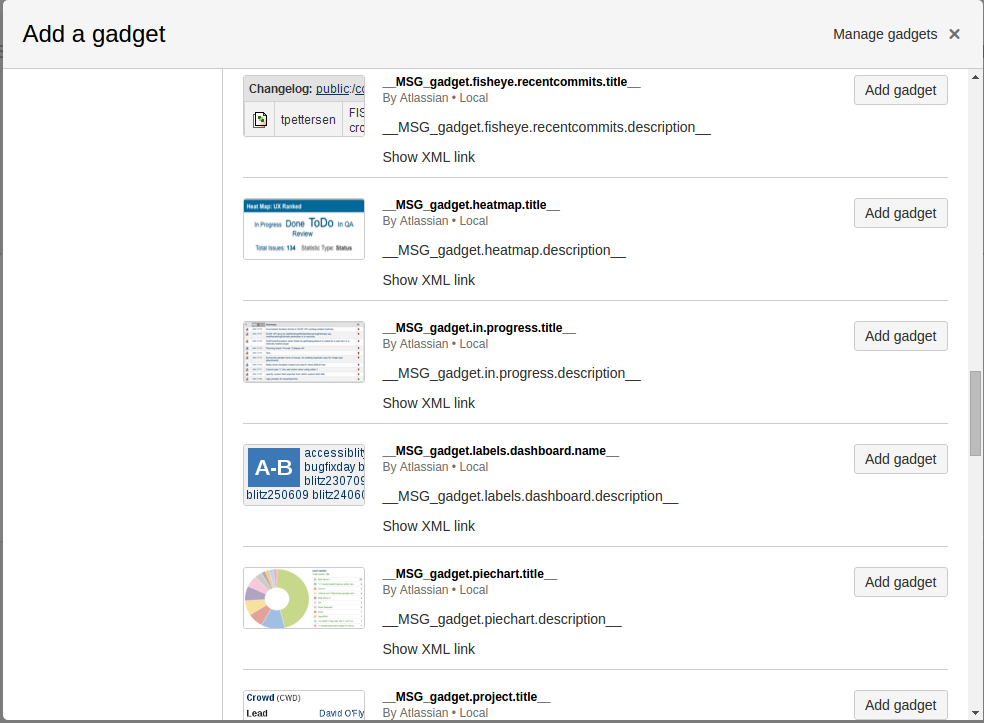
Understanding the Results
Icon | Result | What this means |
|---|---|---|
Green Checkmark | Jira can access itself through the configured Base URL | Your dashboard gadgets should be generated and loaded correctly. |
Yellow Warning Triangle | Jira is not able to access itself through the configured Base URL. This is necessary so that dashboard gadgets can be generated successfully. Please verify the current Base URL and, if necessary, review your network configurations to resolve the problem. | Your dashboard gadgets may not be loading correctly. Please follow the diagnosis and resolution steps below to resolve the problem. |
Diagnosis
Environment
iptables has been configured to forward packets from 80 to 8080 and/or 443 to 8443
From the Jira server itself, try curl -v <baseurl> to verify if JIRA is able to communicate with itself.
Run SSLPoke from the Jira server itself and see if it returns successfully.
Additionally, run the httpclienttest from the Jira server itself to confirm if the SSL configuration is okay.
There are application links configured on the instance but they seem to be having issues.
As the symptoms for both environments are different, diagnosis and resolution steps are segregated into multiple sections below.
Entries have been configured in the hosts file.
Cause
When accessing the Dashboard, the gadgets serve a response that is processed by the client (ie the browser) to generate gadgets. While this happens, the server also connects to itself to provide the gadget's translated strings. Jira uses the URL the instance is connected to, so the Jira instance needs to be able to access itself.
Without Usage of Proxy
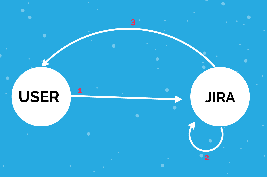
The user sends a request to Jira on loading the Dashboard
Jira will perform a call towards itself through the gadget URL.
Jira replies with the completed page and gadget's translated strings
With Usage of Proxy
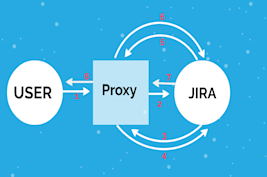
1. The user sends a request to Jira on loading the Dashboard
2. Proxy forwarded this request to Jira
3. Jira will perform a call back to itself through the gadget URL to get the gadget's title. Performing requests to Proxy
4. Proxy forwarded this request back to Jira itself to provide the gadget's translated strings
5. Jira replies gadget's translated strings to the proxy
6. Proxy forwarded this accordingly to Jira
7. Jira replies with the completed page to proxy
8. Proxy forwarded this accordingly to use
If it's not able to do so this error will occur.
Some known causes are:
Basic or certificate-based auth on a proxy layer that Jira is behind
The domain name is not resolvable
Jira is served on an IP that's in a separate restricted subnet to the server Jira is running on
Jira is served with a self-signed certificate that doesn't exist in its own trust store
There are more than 3 redirects between the entry point and the final Jira server (this is tested in the base URL check and also configured in our gadgets).
The recommended best practice is to have Jira served on one domain name only. This can have different IPs (for example internal and external) configured by different DNS, however will only resolve to one domain. For example, https://jira.atlassian.com has an external IP of 131.103.28.11 (mapped to by external DNS) and an internal IP of 192.168.1.2 (mapped with an internal DNS). It has one certificate for that FQDN, and all users access it on that domain only.
Additionally, there are some environmental-specific causes of this problem. Please see below for further information.
Solution
Cause 1:
Jira applications with SSL Configured
The following appears in the atlassian-jira.log file:
1
2
3
2016-02-26 14:22:28,843 http-bio-8443-exec-11 ERROR admin 862x395x1 m32d6k xx.xx.xx.xx /secure/MyJiraHome.jspa [c.a.g.r.internal.http.HttpClientFetcher] Unable to retrieve response
javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
at sun.security.ssl.Alerts.getSSLException(Alerts.java:192)Cause1
2
3
4
5
6
7
2022-03-29 23:14:36,116-0700 HealthCheck:thread-1 ERROR ServiceRunner [c.a.t.j.healthcheck.support.GadgetFeedUrlHealthCheck] An error occurred when performing the Gadget feed URL healthcheck
javax.net.ssl.SSLException: Connection reset
at sun.security.ssl.Alert.createSSLException(Alert.java:127)
at sun.security.ssl.TransportContext.fatal(TransportContext.java:324)
at sun.security.ssl.TransportContext.fatal(TransportContext.java:267)
at sun.security.ssl.TransportContext.fatal(TransportContext.java:262)
at sun.security.ssl.SSLTransport.decode(SSLTransport.java:135)Resolution
Verify that the Root and Intermediate CA certificates were added to the keystore when SSL was configured
Follow our instructions in our Unable to Connect to SSL Services Due to 'PKIX Path Building Failed' Error knowledge base article for additional details to resolve the problem.
Restart Jira (if Data Center, restart all nodes one by one)
Additionally, verify the configuration with httpclienttest as described in the readme of that repository, to gather more detail.
Cause 2: Jira Applications with port forwarding configured
This applies to environments that are using port forwarding, such as iptables:
If port forwarding has been configured to forward packets from 80 to 8080 and/or 443 to 8443, you may see gadget titles be broken and show as __MSG_gadget.xxxxxxx. This can happen if the rules are configured only to forward packets from external sources.
Resolution:
You need to create a rule both for packets coming from external IP sources AND for local packets.
For example, in iptables, it should look like this:
1
iptables -t nat -I OUTPUT -p tcp -o lo --dport 80 -j REDIRECT --to-ports 8080For firewalld:
1
2
firewall-cmd --permanent --add-masquerade
firewall-cmd --permanent --add-forward-port=port=80:proto=tcp:toport=8080In Windows, we can use the netsh command, like this:
1
netsh interface portproxy add v4tov4 listenport=80 connectport=8080Cause 3: Jira applications with a broken Proxy configuration
This applies to environments configured to use a Web Proxy. This can be determined by checking the "JVM Arguments" in the System Information screen for existing proxy configurations.
Jira is unable to communicate with itself due to a Web Proxy not being able to correctly resolve the Jira server.
Resolution
Add the Jira server's hostname/ to the -Dhttp.nonProxyHosts and -Dhttps.nonProxyHosts arguments as in Configure an outbound proxy for use in Jira server.
Make sure that the same domain is not being mentioned twice in an argument, e.g. - Dhttps .nonProxyHosts = jira|confluence|jira
Cause 4: Jira configured with Apache in front with BasicAuth password restriction
Cause
Jira is unable to communicate with itself due to a Web Proxy requiring authentication.
Bug ticket: JRASERVER-61273 - Gadgets title broken when JIRA is running behind proxy with authentication.
Resolution
Add the server IP itself for access without a password:
Order Allow, Deny Allow from <hostname> Satisfy Any
Resolution 2
If using Shibbolethauthentication ,
leave the /rest URLs outside the shibbolethauthentication.
/rest URL must not be shibboleth protected.
Example :
1 2 3 4 5 6 7 8 9 10 11 12 13<LocationMatch "^(/rest)/[^/]+"> AuthType None Require all granted </LocationMatch> <LocationMatch "/"> AuthType Shibboleth ShibRequireSession On require valid-user ShibUseEnvironment On Order allow,deny Allow from all </LocationMatch>
Cause 5: Entries have been configured in the hosts file
Sometimes after server migrations, some errors are shown when there's no DNS in function and an entry is not properly configured in the hosts file.
1
2
HealthCheck:thread-3 ERROR [c.a.t.j.healthcheck.support.GadgetFeedUrlHealthCheck] An error occurred when performing the Gadget feed URL healthcheck
org.apache.http.conn.ConnectTimeoutException: Connect to FQDN:443 [FQDN/OLD_IP] failed: connect timed outResolution
Check the hosts file in your server and update the IP:
Linux:
/etc/hosts
Windows:
C:\Windows\System32\drivers\etc\hosts
Cause 6: Incorrect Traffic Shaping on Reverse Proxy or LB for REST API calls
While taking advantage of traffic shaping, customers configure the load balancer to identify all external REST API traffic and send it to a dedicated node. While doing this an incorrect configuration of sending all /rest traffic to a single node will cause background rest calls in Jira pages to be directed to that node. This will cause errors when this dedicated Jira REST API node is not up and running.
Traffic distribution with Atlassian Data Center
Resolution
While doing traffic shaping only configure M2M REST API Calls to the dedicated node, and ensure end-user API calls continue using the same node that user has logged in initially.
Cause 7: "Netscape Certificate Type" Field in the Certificate is only filled with "SSL Client" Type
1
2
2022-02-23 00:11:38,543+0000 HealthCheck:thread-7 ERROR [c.a.t.j.healthcheck.support.GadgetFeedUrlHealthCheck] An error occurred when performing the Gadget feed URL healthcheck
javax.net.ssl.SSLHandshakeException: Netscape cert type does not permit use for SSL serverResolution:
Used Certificate must have set the "Netscape Certificate Type" Field to SSL Server and SSL Client
Was this helpful?