無効な SAML 応答の受信: シグネチャの検証に失敗しました。SAML 応答は拒否されました。
プラットフォームについて: Server および Data Center のみ。この記事は、Server および Data Center プラットフォームのアトラシアン製品にのみ適用されます。
Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Fisheye および Crucible は除く
問題
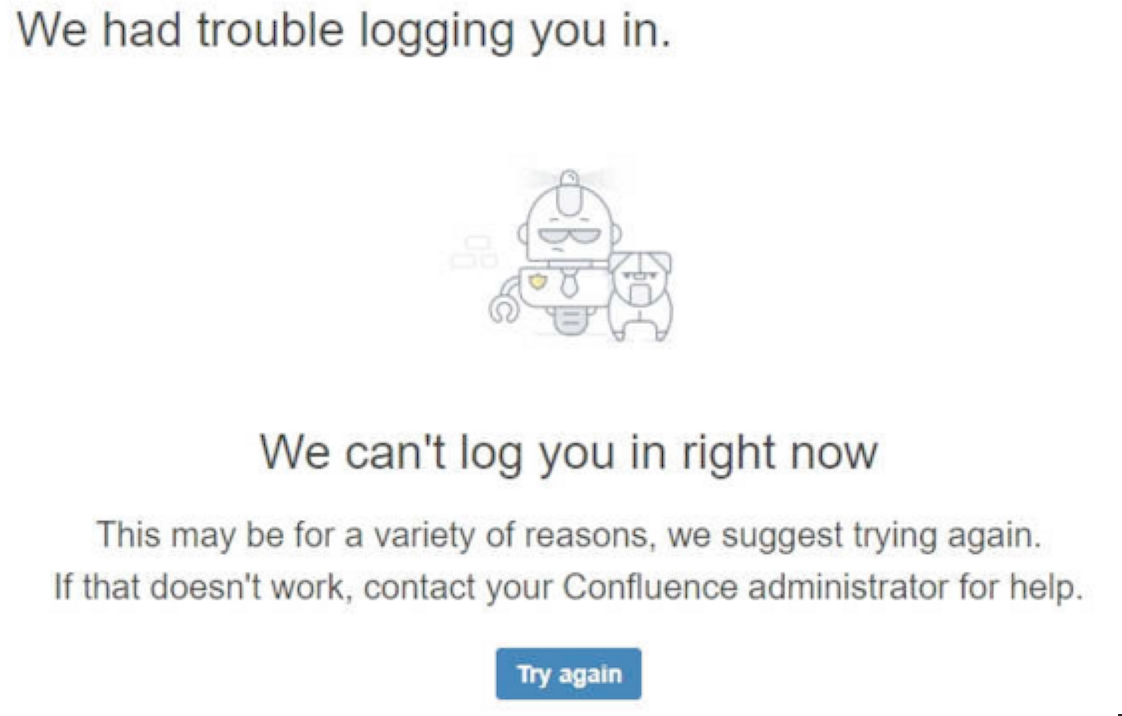
After setting up SAML using the built-in SAML plugin in Confluence Data Center, your users are unable to authenticate and login and receive the following message in the browser:
- We had trouble logging you in. We can't log you in right now. This may be for a variety of reasons, we suggest trying again. If that doesn't work, contact your Confluence administrator for help.
診断
環境
- Confluence Data Center 6.1.x and above
- Using the built-in SAML plugin
- Users cannot login after setting up SAML in Confluence and in the IdP
Log Messages
- After the first failed attempt where you receive the error in the above screenshot, add logging for com.atlassian.plugins.authentication with a level of ALL, then reproduce the issue in your browser.
You should see something similar to this error (your IdP URL will vary) in
<confluence-home>/logs/atlassian-confluence.logERROR ... Received invalid SAML response: Signature validation failed. SAML Response rejected -- referer: http://example.com/pingfederate/idp/startSSO.ping?PartnerSpId=https://confluence.example.com | url: /plugins/servlet/samlconsumer | traceId: d8d652948ef10fa1 | userName: anonymous com.atlassian.plugins.authentication.impl.web.saml.provider.InvalidSamlResponse: Received invalid SAML response: Signature validation failed. SAML Response rejected
原因
2 つの原因が考えられます。
原因 1
Mismatch with the X509 certificate used for signing (the certificate configured in Confluence doesn't match the one used by the IdP).
原因 2
IdP's default is to sign the entire response. The SAML module that Confluence is using is expecting only the assertion portion of the SAML response to be signed.
ソリューション
For cause #1:
Check that the X509 certificate configured in Confluence is the same as the one the IdP uses, which you can retrieve from the SAML response or directly from the IdP. If they don't match, modify the SAML configuration in Confluence with the correct certificate.
For cause #2:
In federation systems, the IdP has the ability to sign the entire response or just the assertion portion of the response (see screenshot below). Configure the IdP to sign only the assertion portion of the SAML response.
Example from PingFederate: