Failures in Automation for Jira rules involving third-party actions
Platform Notice: Data Center Only - This article only applies to Atlassian products on the Data Center platform.
Note that this KB was created for the Data Center version of the product. Data Center KBs for non-Data-Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
With Automation for Jira 9.1.1 update, automation rules that incorporate third-party actions, such as ScriptRunner scripts, are experiencing failures. These failures are noted without further details in the Automation Audit Log as shown below:
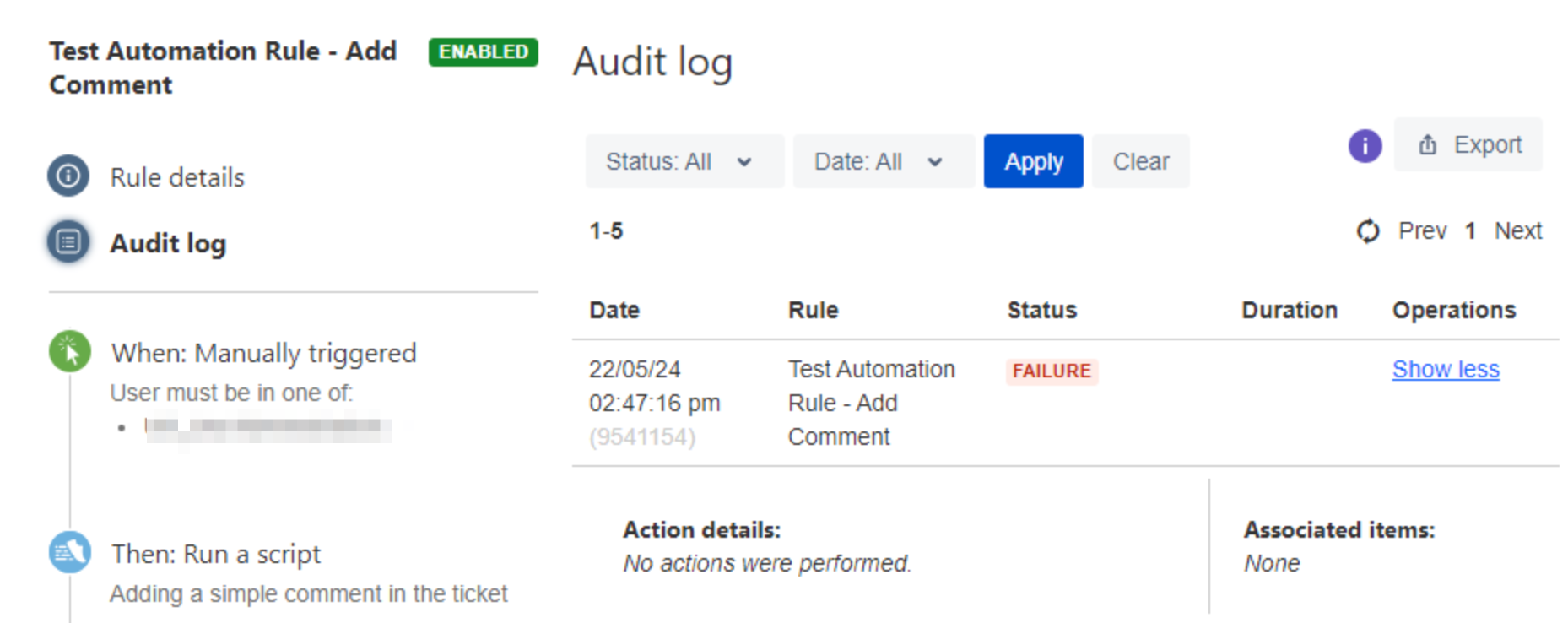
Diagnosis
The problem began after upgrading Automation for Jira to 9.1.1
Upon configuring DEBUG logging level the following two debug packages com.codebarrel.automation and com.codebarrel.jira.plugin.automation, within the atlassian Jira log files, we encountered a message stating: "has been skipped because it didn't pass the validation."
ATLASSIAN-JIRA.LOG
12024-05-31 08:30:00,671+0000 http-nio-8080-exec-25 url: /jira/rest/cb-automation/latest/project/10000/rule/1/execute/SCRUM-23; user: admin DEBUG xxx 510x1768x1 xxxx /rest/cb-automation/latest/project/10000/rule/1/execute/SCRUM-23 [c.c.j.p.a.service.execution.JiraAutomationExecutionService] Sync execution of Rule(id=1, name='Sample Scriptrunner rule') for AutomationEvent with traceId='d105dd50-1017-4ca5-900c-8576261cba33' has been skipped because it didn't pass the validation.Rule actor lacks the global Jira Administrator permission
Cause
Scriptrunner's "run a script" and many other third-party plugin actions require Jira admin permission. However, in earlier versions, this requirement was not adequately validated and was only implemented after the Jira 9.1.1 update.
Several bugs / improvement requests are related to this behaviour:
The Automation Audit log failure message doesn’t have additional details about failure reasons: JIRAAUTOSERVER-1029
No validation happening while trying to publish rule where Actor user has insufficient permissions: JIRAAUTOSERVER-1030
Documentation improvement on which permission is required for 3rd-party plugin-provided actions: JRASERVER-77784
No email is sent to notify the rule owner of the rule failure: JIRAAUTOSERVER-1100
Solution
To fix all the automation rules impacted by this issue, we need to grant global Jira Administrator permission to their rule actor, by following the steps below:
Identify all the automation rules that are using an action coming from a 3rd party add-on via the Jira Database by using the SQL query below (the result will include the Rule Names and IDs):
SQL Query Postgres:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
SELECT
r."ID" AS "Rule Id",
r."NAME" AS "Rule name",
t."TYPE" AS "Rule trigger",
STRING_AGG(DISTINCT p.pkey, ', ') AS "Project Keys",
au1.lower_user_name AS "Rule author",
au2.lower_user_name AS "Rule actor"
FROM "AO_589059_RULE_CONFIG" r
LEFT JOIN "AO_589059_RULE_CFG_COMPONENT" t ON t."RULE_CONFIG_ID" = r."ID" AND t."COMPONENT" = 'ACTION'
LEFT JOIN "AO_589059_RULE_CFG_PROJ_ASSOC" rp ON rp."RULE_CONFIG_ID" = r."ID"
LEFT JOIN project p ON CAST(p.id AS TEXT) = rp."PROJECT_ID"
LEFT JOIN app_user au1 ON au1.user_key = r."AUTHOR_KEY"
LEFT JOIN app_user au2 ON au2.user_key = r."ACTOR_KEY"
WHERE r."STATE" = 'ENABLED'
AND t."TYPE" not in ('jira.issue.assign'
'jira.issue.clone',
'jira.issue.comment',
'jira.issue.create',
'jira.issue.create.subtasks',
'jira.issue.delete.comment',
'jira.issue.delete',
'jira.issue.delete.link',
'jira.issue.edit',
'jira.issue.link',
'jira.worklog.add',
'jira.issue.add.watcher',
'jira.issue.transition',
'jira.issue.outgoing.email',
'hipchat.notification',
'msteams.notification',
'slack.notification',
'stride.notification',
'twilio.notification.sms',
'jira.issue.outgoing.webhook',
'jira.sd.add.customer',
'jira.sd.create.request',
'jira.version.create',
'jira.version.release',
'jira.version.unrelease',
'jira.create.variable',
'jira.issue.deleteattachment',
'codebarrel.action.log',
'jira.lookup.issues',
'jira.publish.event',
'jira.issue.refresh.issue',
'jira.set.entity.property',
'jira.issue.archive')
GROUP BY
r."ID", r."NAME", t."TYPE", au1.lower_user_name, au2.lower_user_name
ORDER BY
r."NAME" ASC;SQL Query Oracle:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
SELECT
r.ID AS "Rule Id",
r.NAME AS "Rule name",
t.TYPE AS "Rule trigger",
LISTAGG(DISTINCT p.pkey, ', ') WITHIN GROUP (ORDER BY p.pkey) AS "Project Keys",
au1.lower_user_name AS "Rule author",
au2.lower_user_name AS "Rule actor"
FROM AO_589059_RULE_CONFIG r
LEFT JOIN AO_589059_RULE_CFG_COMPONENT t ON t.RULE_CONFIG_ID = r.ID AND t.COMPONENT = 'ACTION'
LEFT JOIN AO_589059_RULE_CFG_PROJ_ASSOC rp ON rp.RULE_CONFIG_ID = r.ID
LEFT JOIN project p ON p.id = rp.PROJECT_ID
LEFT JOIN app_user au1 ON au1.user_key = r.AUTHOR_KEY
LEFT JOIN app_user au2 ON au2.user_key = r.ACTOR_KEY
WHERE r.STATE = 'ENABLED'
AND t.TYPE not in ('jira.issue.assign','jira.issue.clone','jira.issue.comment','jira.issue.create','jira.issue.create.subtasks','jira.issue.delete.comment','jira.issue.delete','jira.issue.delete.link','jira.issue.edit','jira.issue.link','jira.worklog.add','jira.issue.add.watcher','jira.issue.transition','jira.issue.outgoing.email','hipchat.notification','msteams.notification','slack.notification','stride.notification','twilio.notification.sms','jira.issue.outgoing.webhook','jira.sd.add.customer','jira.sd.create.request','jira.version.create','jira.version.release','jira.version.unrelease','jira.create.variable','jira.issue.deleteattachment','codebarrel.action.log','jira.lookup.issues','jira.publish.event','jira.issue.refresh.issue','jira.set.entity.property','jira.issue.archive')
GROUP BY
r.ID, r.NAME, t.TYPE, au1.lower_user_name, au2.lower_user_name
ORDER BY
r.NAME ASC;Open the configuration page of each automation rule and check the rule actor
You have 2 options to fix the automation rule and ensure that the rule actor is granted the global Jira Administrator permission:
Option 1:
Keep the rule actor as it is
Add this user to the right group that is will grant them the Global Administrator permission via the page
⚙ > User Management > Users
Option 2:
Change the rule actor to another user who was already granted the Global Administrator permission
To be able to change the rule actor, the user who will make the change to the rule configuration needs to be granted the permission Impersonate users in A4J global scope
within the project permission scheme, if the rule has 1 project in its scope
at the global Jira level, if the rule has at least 2 projects in its scope
Was this helpful?